Caleb

The account system here is a little bit wonky. I understand some of the technical benefits, but not working how people expect (how every other user account system works) will eventually have its own cost.
In the mean time at least one technical aspect should be dealt with asap. The short lifetime PIN for validating another sessions is okay if both devices are at hand, but often that is not the case. Hence the recovery code will get used a lot, and saved, and passed around between computers by who knows what mechanism. Mistakes happen. These will get compromised. If you don't believe me:
6a2271e8-2f4c-663b-43ac-2e245414fedd
Yes that's my actual account recovery code — before I fiddled with it and typed over some hex values.
The point is that "treating something like a password" doesn't mean it will stay private. Just a couple months ago a series of mistakes with my password manager and its autotype mechanism led me to post my real SE password into an SE chat session. Thankfully somebody pointed this out and I reset the password and all sessions in a hurry, but mistakes happen. Recovery codes should not be permanent any more than passwords. A mechanism to reset them is required.
Top Answer
Jack Douglas

> A mechanism is needed to invalidate account recovery codes.
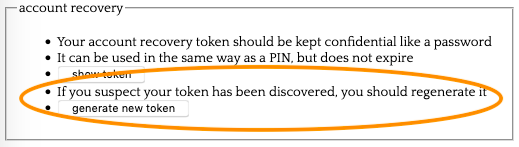
Thanks for suggesting this, I think you were right that it's urgent to get a mechanism in place.
We've just rolled out the feature:
> Yes that's my actual account recovery code — before I fiddled with it and typed over some hex values.
I suggest you test the feature now :P
Answer #2
Paul White

It does make sense to allow a user to generate a new recovery token. That action should invalidate the previous token.
>...but not working how people expect (how every other user account system works) will eventually have its own cost.
I think the benefits of not storing an email address outweigh that cost.